INTRODUCING MERAKI TRUSTED ACCESS

The Easiest Way to Grant Secure Access to Devices
These days, as individuals carry multiple types of devices and expect to be connected at all times, the job of an IT admin becomes more complicated and stressful. Knowing what each end-user and device is trying to do on the network can be a burden. How can you feel confident that your network security will not be jeopardized while company assets remain contained?
Systems Manager, Cisco’s Mobile Device Management (MDM) solution, is evolving to address this need. We are introducing Meraki Trusted Access, which securely connects personal devices to business-critical resources without requiring an MDM profile to be installed.
Meraki Trusted Access enhances both the IT and end-user experience
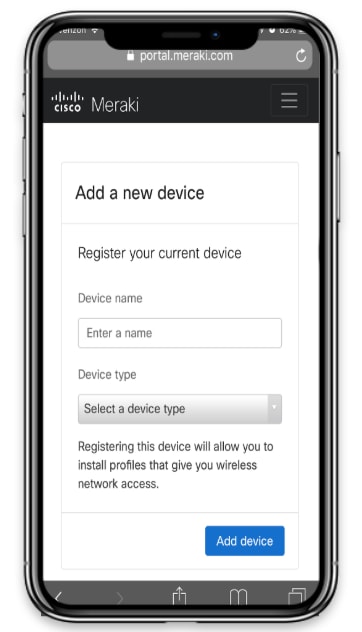
For IT, Meraki Trusted Access means no longer dealing with tedious and manual onboarding processes. Granting secure network access to end devices becomes seamless and automated. With the Meraki dashboard, IT can sync their Active Directory server to create user profiles. From those user profiles, Trusted Access can then be enabled for specific Wi-Fi networks, specifying how many devices each user can onboard to get access and for how long. A user’s device gets access using a certificate, once that user is authenticated, the device is now “trusted”. A “trusted” device can now securely access resources.
Additionally, Meraki Trusted Access enables more control and manageability over certificate-based onboarding processes. Whether a user is managed or unmanaged, the certificate authentication is done with Meraki. This removes the need to engineer complex third-party integrations. Finally, Systems Manager also offers an open API platform for customized integrations, for more business-critical operations.
For end-users, Meraki Trusted Access means an easier way to access critical applications. By using the newly enhanced Meraki Self-Service Portal, end-users can sign into the portal and start onboarding their devices themselves. From there, they can download certificates directly to those devices, granting them secure access to business-critical applications they might need. On top of this intuitive method of getting their devices access, end-users will also be happy to know that their privacy stays intact. They will no longer need to enroll into an MDM solution in order to get the access they need.
Meraki Trusted Access is the easiest way to securely connect devices without an MDM
Enabling Meraki Trusted Access is simple. Meraki Trusted Access is enabled when you have both Meraki MR access points and Meraki Systems Manager in your network.
You can configure Meraki Trusted Access in 4 simple steps:
- Enable Trusted Access on an SSID
- Create an end-user profile under Systems Manager. You can automatically use Active Directory group tags to enable Trusted Access or configure users manually.
- Select the end-user’s network access privileges and tie them to the SSID that has Trusted Access enabled
- Share the Self-Service Portal link to the end-user so they can onboard their devices and download the trusted certificate.
Cisco’s MDM solution, Meraki Systems Manager, continues to provide end-users and end-devices network security with flexible authentication methods, automated device onboarding, and dynamic security policies.
If you are a current MR and SM customer, you can try Meraki Trusted Access today (just make sure you have enough SM licenses to cover the number of mobile devices). Start by reading our Meraki Trusted Access documentation guide for a smooth set-up. If you’d like to learn more aboutSystems Manager, you can connect with the Meraki team to start a 30-day free trial, no strings attached.














Dell Software Group sold to help fund looming EMC deal
Ingram Micro gets distribution access to Dell’s security range in Australia