SonicWALL – EDUCATION INSTITUTION WEBSITE UNKNOWINGLY SERVING NEW VARIANT OF PHOBOS
The SonicWall Capture Labs Threat Research Team observed reports of a new variant of the Phobos ransomware trojan being served via a blog on a major education institution. A publicly accessible listing of one of the blogs subdirectories shows that the Phobos malware executable file had been recently uploaded. Phobos, a combination of both the CrySiS and Dharma ransomware families has been in operation since mid-December 2018. We have chosen to keep the identity of the website anonymous.
The issue was reported on Twitter:

The directory listing for the website shows the presence of the malware:

The malware was publicly accessible on the website for just over 2 weeks. It is now inaccessible.
Infection Cycle:
The trojan uses the following icon:

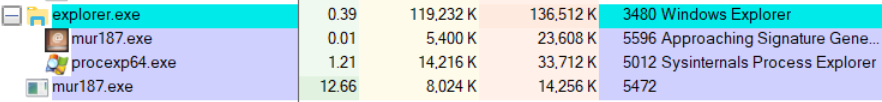
Upon initial infection, the malware can be seen running in the process list and using considerable CPU resources as it encrypts files in the background:
It encrypts files on the system and appends “.id[{file id value}].[[email protected]].banjo” to their filenames. eg.
mynotes.txt.id[78B73C19-2288].[[email protected]].banjo. The previous variant uses a .Phobos extension.
It drops the following files onto the system:
- info.txt (to desktop and shared drives)
- info.hta (to desktop and shared drives)
- %PROGRAMDATA%\Microsoft\Windows\Start Menu\Programs\Startup\mur187.exe
info.txt contains the following message:

info.hta contains the following page. Multiple instances of the page are displayed on the desktop after the initial encryption phase. Any subsequent new files that are created on the system are also instantly encrypted. This page is almost identical to that of Dharma and CrySiS ransomware:
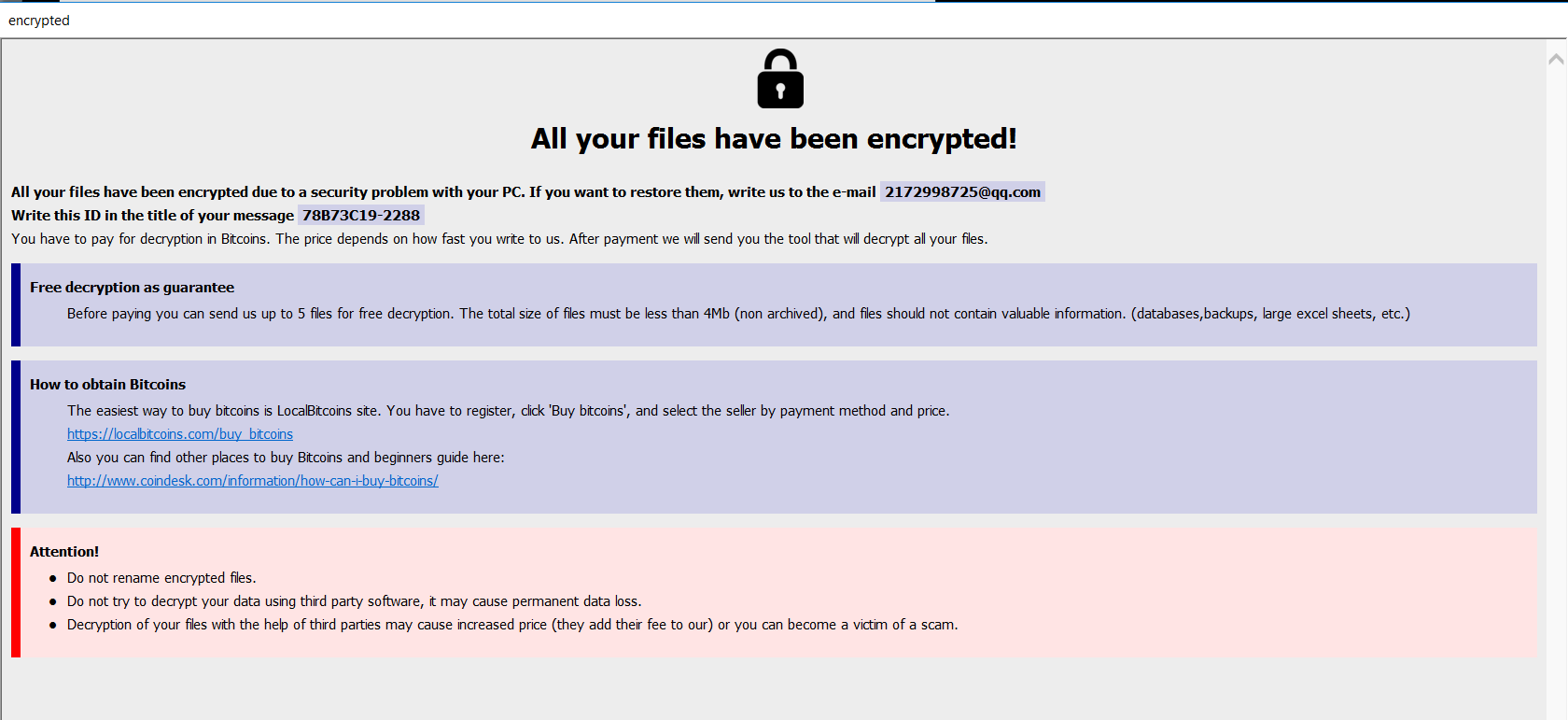
Unlike the previous variant, there is no Phobos branding on the help page. The email address has also changed. We speculate that this variant has been created by the same group propogating CrySiS and Dharma ransomware.
We reached out to [email protected] to ask how to retrieve files but received no reply.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Phobos.BN (Trojan)
- GAV: Phobos.RSM_2 (Trojan)
- GAV: Phobos.RSM_3 (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.













Dell Software Group sold to help fund looming EMC deal
Ingram Micro gets distribution access to Dell’s security range in Australia