From Homes to the Office: Revisiting Network Security in the Age of the IoT
The internet of things (IoT) has gone beyond the walls of the “house of the future” and is quickly finding its way into businesses, as many enterprises have come to recognize its potential in providing a myriad of solutions for their growing needs. Taking advantage of this rapidly developing technology, businesses began adopting for their network environments devices that are typically used in home settings, belatedly realizing an underlying concern: network and data security.
One factor complicating this security concern is the burgeoning remote working trends accommodated by companies to maximize employee productivity. The IoT devices connected to public networks have become prime targets of malicious actors wanting to compromise enterprise systems and/or disrupt business operations by launching inbound or outbound attacks, tracking high value targets’ movements and patterns, or stealing proprietary information and personal data of customers and employees.
According to research estimates from Gartner, IoT devices are poised to outnumber the world’s population by 2020. Unchecked, this exponential growth is projected to impact enterprise network security significantly – with as much as 25% of identified attacks coming by way of IoT devices and related technologies. Attackers are finding more ways to get into businesses’ networks and data, profiting from these unauthorized intrusions via the weak security protocols of these devices.
Here are the commonly used features and types of home devices in the market today, the risks that attackers can take advantage of, and the best practices to defend and mitigate against attacks.
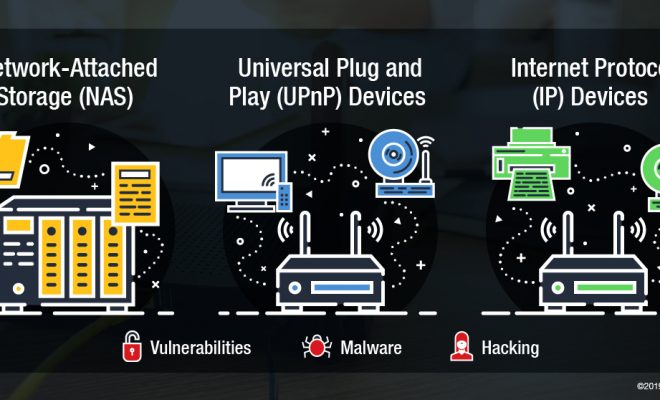
Network-attached storage (NAS)
Network-attached storage (NAS) enables multiple users and devices to access data through an intranet, local area network (LAN), mobile or broadband. Its capacity allows enterprise and home users to support high volume tasks, archiving, automation, file sharing, backup, and – for many of the newer models – a cloud-support capable feature, suitable for work teams in distributed locations and time zones.
Risks and Threats: In 2014, ransomware SynoLocker specifically went after a particular brand of NAS devices after attackers modified a version of Cryptolocker ransomware. Encrypting their files, victims were told to pay up within a specified number of days in exchange for the decryption code to retrieve access to their hardware. More recently, a number of malware have evolved to include routines targeting routers and devices such as 2018’s VPNFilter, its modular feature capable of infection routines on various stages and persistence.
A quick search via Shodan in 2015 by HKCERT showed exposed NAS devices facing the internet in Hong Kong. As most NAS devices only require simple authentication, default or weak usernames and passwords can be brute forced by attackers to gain access into the system, inevitably allowing malicious actors to access all admin or user rights and settings changes. The same brand of NAS devices attacked with SynoLocker in 2014 were targeted more recently with eCh0raix, with attackers suspected of scanning for exposed devices and launching dictionary attacks.
As discovered by a white hat in 2015, vulnerabilities in the devices themselves can be used by attackers. By exploiting unpatched flaws in devices connected to the internet, attackers gain full control over files or revise device encryption keys before submitting it back to the server, preventing legitimate users from accessing their files. In August this year, reports state that some eCh0raix ransomware variants are also going after specific Quality Network Appliance Provider (QNAP) NAS appliance vulnerabilities; all of the devices become susceptible to the said attacks regardless of the device’s model number because they are running on the same operating system.
Best practices: Ensure that teams with critical operational roles keep backup copies of important files. If possible, keep NAS disconnected from the internet until a security solution, such as software updates, become available. IT teams should keep device firmware updated with patches from legitimate vendors. Moreover, ensure that network authentication processes are periodically changed and access credentials are updated. In the event that these security measures fail and systems are infected by ransomware, never give in to attackers’ demands as there is no assurance that these cybercriminals will keep their word.
Universal Plug and Play (UPnP) devices
Almost all IoT devices today are equipped with a Universal Plug-and-Play (UPnP) feature that enables networked devices to “find and communicate” with each other to share data and functions. While primarily intended for residential networks and use, vendors have encouraged this feature to be present and set at default in most consumer devices for ease of use and accessibility, as opposed to manually setting up and forwarding ports one by one.
Risks and Threats: Because of the automated protocol used by these devices, UPnP devices can easily bypass the firewall and deliver malware to the router, potentially delivering malicious programs directly to all other devices connected to it. In 2016, Mirai was discovered infecting smart homes and consumer devices – such as IP cameras and home routers – to turn them into a part of a remotely controlled botnet. The discovery highlighted security gaps and loopholes in the operating systems used by home routers and IoT devices, popularly chosen by device manufacturers for its cost-effectivity and portability. In 2017, while working on another set of UPnP discoveries, researchers found a new family of injections named EternalSilence, leveraging a family of exploits to open systems and facilitate other attacks from the same malware family.
More recently, hackers took advantage of misconfigured routers to stream a YouTube video via a number of smart home devices in March, telling viewers to subscribe to PewDiePie’s channel. The ports involved in the attack are specific to the management of functions of the internally connected devices, and their incorrect configurations exposed them to the internet upon scanning.
And despite the changing models and number of brands released in the market today, many of the devices released to date use old versions of the software or legacy systems, such as MiniUPnP daemon for network address translation (NAT) to provide port mapping protocol services and Windows XP-based UPnP. As documented by Trend Micro, old versions of the daemon and end of life-based machines need to be patched for high-risk vulnerabilities.
Best practices: Remote workers should change the default settings of devices such as login credentials to make them less vulnerable to unauthorized access. IT and security teams must encrypt wifi connections and enable the router’s firewall to keep network piggybackers out. Disable unnecessary components in the router — such as UPnP — unless otherwise needed in order to prevent malicious actors and malware from leveraging these features for outbound attacks like botnets. Install and enable security layers in routers such as intrusion prevention systems, and avoid using white-label or used routers that may be improperly configured or come with embedded backdoors.
Internet Protocol (IP) devices
Internet protocol (IP) devices send or receive data via LAN and/or the internet, and are increasingly being adopted by enterprises for their resolution, easy installation and scalability, as well as the analytics they afford. Popular IP devices such as cameras and printers enable users to easily connect their computers to these devices – as well as its related peripherals, also due to their UPnP protocols – via the local network, wifi, or Bluetooth – and use it instantly.
Risks and Threats: IP devices typically come with default settings and credentials so they can easily be used out-of-the-box, which users often forget – or simply ignore — to change, making them a common and preferred target by cybercriminals. TheMoon, first appeared in 2014 and is now one of the oldest malware targeting IoT devices, continues to upgrade its attack methods and exploits of new vulnerabilities. Persirai remains as one of the most persistent IoT botnets that specifically targets IP cameras due to their vulnerability once connected online. Persirai’s discovery comes in the heels of the destructive Mirai’s and Hajime’s distributed denial of service (DDoS) attacks in 2016.
Since these devices are always connected to the internet, their idle computing power masks malicious activities by hackers, making it difficult for users to notice. Trend Micro Research documented how IP cameras in homes and businesses can be hacked into to gather information from unsuspecting owners. Connected printers are also a target in the cybercriminal underground, serving as entry points for various attacks on business and home networks.
Recently, a security flaw in the peer-to-peer communications technology was reported. The attack allowed unauthorized users to access devices remotely without any detection or change in the firewall settings. POODLE vulnerability remains a prevalent flaw in routers and printers that, when exploited, enables the attacker to decrypt encrypted traffic they are able to capture.
Best practices: IT managers can come up with policies that heighten device monitoring and audit, such as the registration of devices with the respective IT teams before they can be used in the office and connected in the network. Accompanying this registration, employees can be advised by the security team that IP device users should change default passwords before installation and use. If unnecessary, UPnP on routers within the company premises should be disabled to prevent devices within the network from opening ports and open to the internet without any warning or authorization. Employ the principle of least functionality, wherein all unnecessary components and ports are closed or removed, and leaving only the needed features active. When recommending new hardware for the company, choose products with accompanying services from manufacturers and vendors that regularly check and update their device software and firmware to minimize cybercriminals’ chances of exploiting security flaws and access to the network.
Conclusion
Protecting networks at home and in the office involve some of the simplest preventive measures, such as purchasing devices from legitimate vendors and retailers who highlight security as one of the foremost features in their products. Changing default credentials of devices, from router password to each connected device’s distinct access codes, can also be one of the first layer of defenses. Closing or disabling unnecessary device components can prevent a number of inbound infections and outbound attacks. Moreover, installing a multilayered security solution can deter even the most sophisticated malware routines.
Work-provided devices are usually not equipped with high-gain antennas and are generally intended for use within company premises; therefore, long-range network signals are not needed. Enterprises and IT teams can limit wifi signal strength in order to keep away unauthorized users outside the immediate office premises from accessing it. Most of all, raising the awareness of employees on having a security-first mindset not only benefits the business but also for their respective homes.
While it is highly imperative for customers to employ security protocols in using their devices, these measures are only as good as the products purchased. Thus, choose products from manufacturers and vendors that give prime importance to user data and network security features during product conceptualization, and ensure that these offerings address or — at the very least — are ready to combat existing threats before releasing them to the market. In and out of the office, instilling a mindset of security-by-design is necessary to keep abreast with the increasing dangers brought about by the rapidly growing demand for IoT today.
[Trend Micro Security News https://bit.ly/2mkihgk]












Dell Software Group sold to help fund looming EMC deal
Ingram Micro gets distribution access to Dell’s security range in Australia